Software Security Intelligence Research Cluster
Empowering Developers to Deliver Secure Software.
According to a recent report, organisations witnessed over 20k newly reported vulnerabilities in 2021 alone. Also, in the last 2 years, more than 60% of the security breaches are due to unpatched vulnerabilities, suggesting that developers of such systems were not aware of the ever-increasing vulnerabilities to fix them in time.
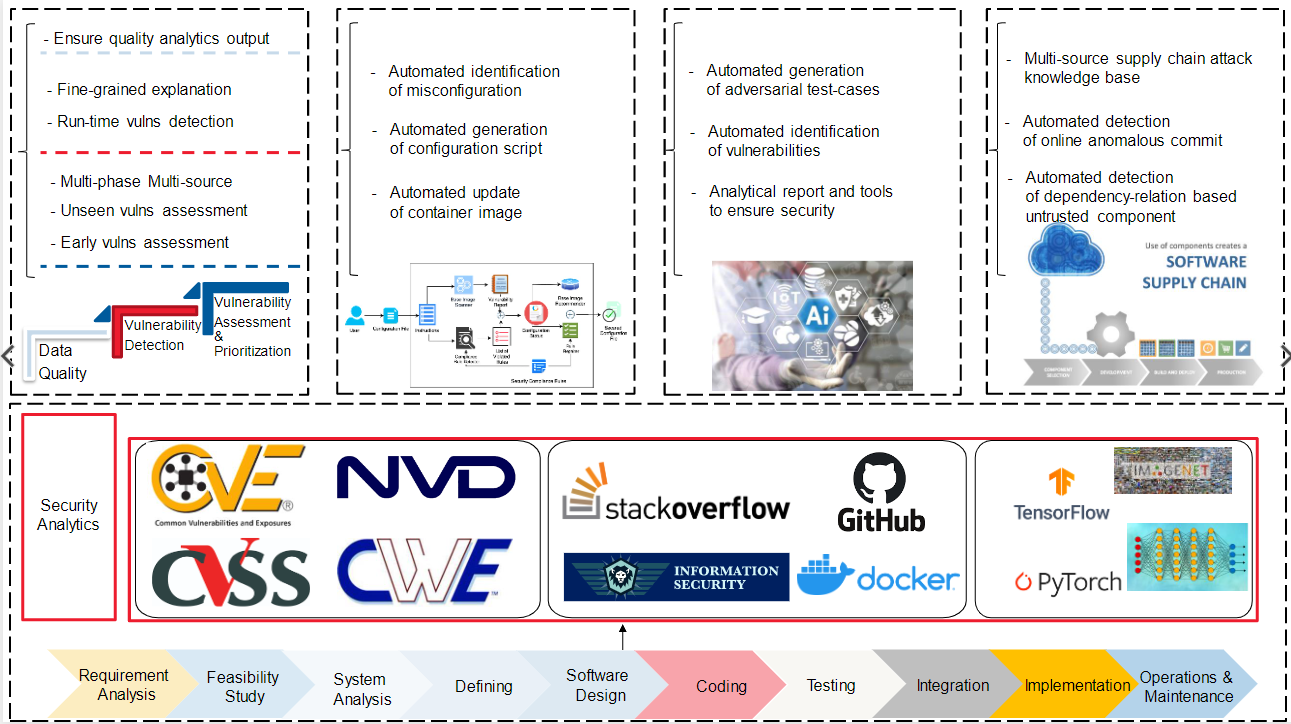
The vision of the Software Security Intelligence (SSI) cluster is to have an all-in-one smart security intelligence platform that gives early warnings and up-to-date information about the latest security vulnerabilities in software systems as well as provides in-time support to mitigate those vulnerabilities for both expert and non-expert users.
To achieve that vision, our research focuses on developing automated techniques to gather, detect, assess and mitigate security vulnerabilities using state-of-the-art Artificial Intelligence enabled technologies like Machine Learning, Deep Learning and Natural Language Processing. All of these developed techniques will be integrated into our unified platform to provide all-in-one security solutions for tackling vulnerabilities.
Such a platform will enhance the cybersecurity for both Australian and worldwide organisations in various industries such as business, defense, mining and space that are using open-source software or developing in-house systems, which in turn reduces the security risks for millions of users using these systems.

















